Computer Security Model Diagram Network Security Diagrams So
Mappa mentale del quadro di sicurezza informatica Home security system Security model
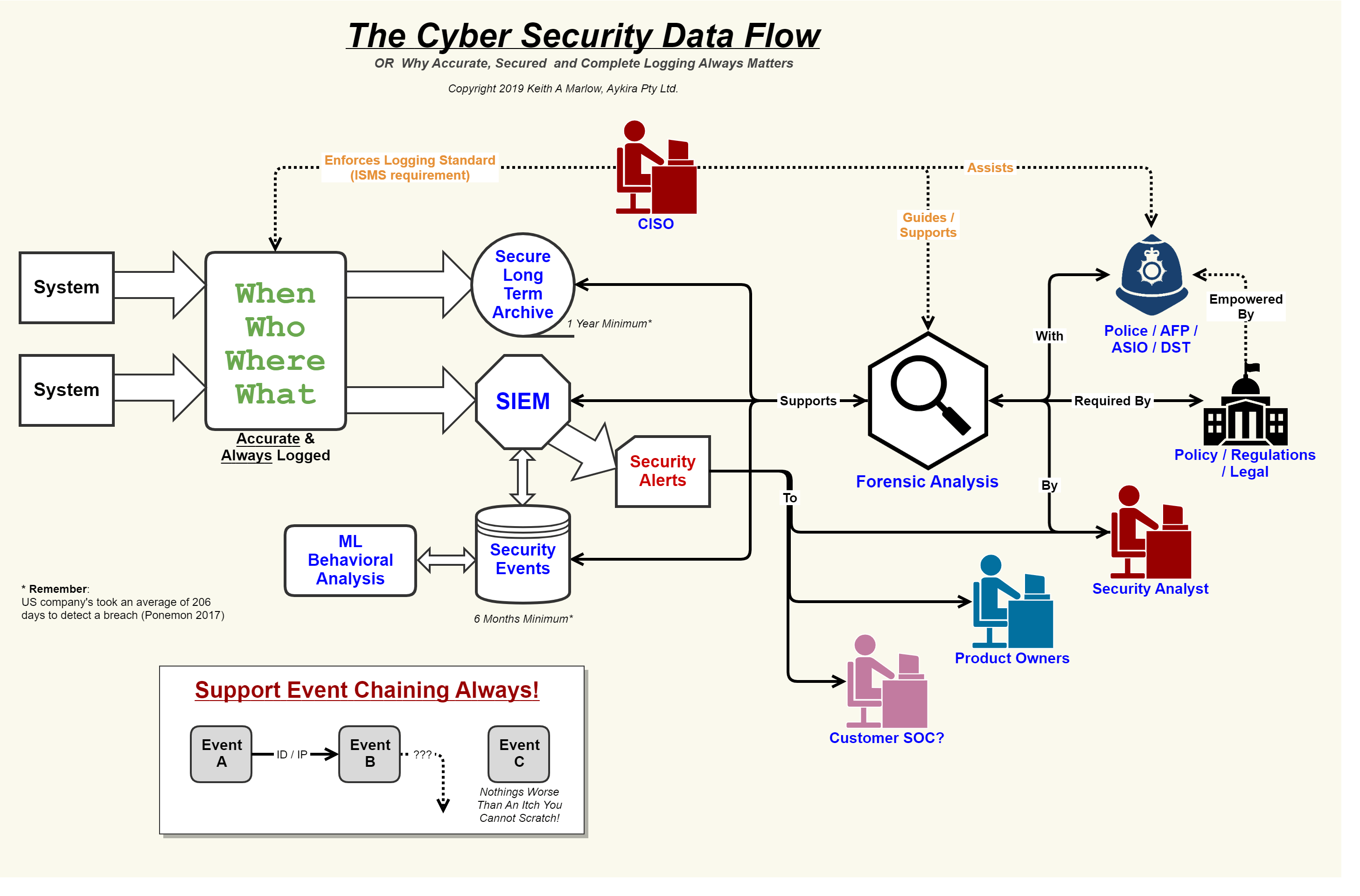
Security Event Logging, why it is so important – Aykira Internet Solutions
Security event logging, why it is so important – aykira internet solutions Security cyber network tips cybersecurity computer infographic steps diagram degrees diagrams example conceptdraw networks solutions architecture information risks threats examples Business intelligence strategy and roadmap ppt
Structure of proposed network security model
Security cyber network tips cybersecurity computer infographic steps diagram degrees diagrams example conceptdraw networks solutions architecture information risks threats examplesThe security network diagram. Network security diagram firewall wireless computer diagrams wan example secure architecture lan networks networking clipart between devices conceptdraw drawing systemComputer diagram security network networking.
Security network diagram architecture firewall example computer diagrams cyber clipart model networks conceptdraw recommended microsoft access examples solution devices infrastructureNetwork security diagram firewall wireless computer wan diagrams secure lan architecture networks example networking drawing between clipart conceptdraw system cyber Network security diagramsSimplified 202a procedural rtca.

Networks diagrams encryption conceptdraw system flow controls protect explain premise flowchart san defines policies communications users audit flowcharts
Help desk support model diagramIndustrial control system Security flow data cyber event logging diagram internet logs important why so together showing concerning events au puttingGovernment conceptdraw diagrams functional thesis cybersecurity involving manual essays networks.
Computer networking: part v: other aspects of computer networkingNetwork security diagrams solution Pin on security hacksIt security solutions.

Network security diagrams solution
Security presentation computer model ppt powerpoint slideserveSecurity diagram system block systems circuits alarm typical basic low electronics part burglar features type cost showing figure Security electronics systems and circuits — part 7Notion cybersecurity template.
Simplified example of a security architecture with different types ofComputer security model What is network security model in cryptography?Security network model computer information ppt powerpoint presentation slideserve suitable.

Network security diagrams
Cyber security degreesNetwork security diagram template Network diagram lucidchart security template topology wan lan area local examples chart networking firewall management templates wide gif storage networksRouter ip settings.
Comptia network+ tutorial: module 05, part 04: wireless network threatsSystem control industrial scada ics does definition process security function trendmicro trend enterprise level Security network model cryptography information sender communicating presents parties two figure helpNetwork security architecture.

Network security firewall diagram wireless computer diagrams wan architecture secure example lan clipart networks between networking software conceptdraw types drawing
System security wiring diagram alarm output hardware software gif input information lcd blockdiagram sensors finalprojects ece ece4760 cornell courses s2004 .
.